Login to Admin console and navigate to JMX Policy Editor Page.
Console -> Security Realms -> myrealm -> Roles and Policies -> Realm Policies -> Click on “JMX Policy Editor”.
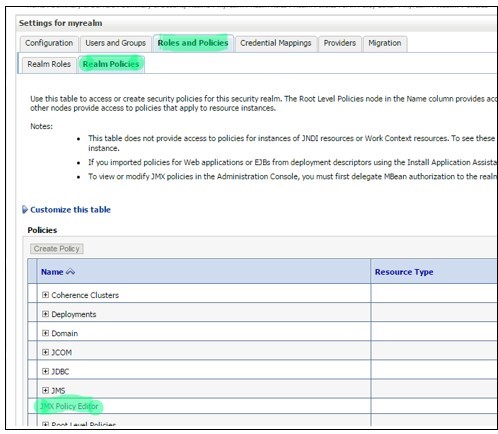
-
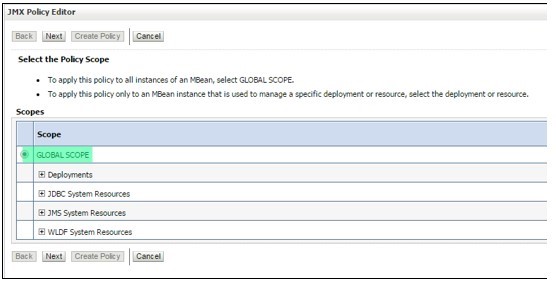
- Select “Global Scope” and click “Next”.
-
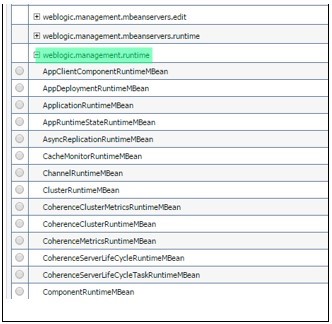
- Expand “weblogic.management.runtime”, select“JMSDestinationRuntimeMBean“and click next.
-
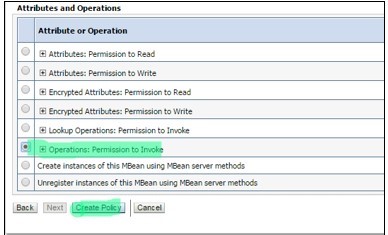
- In Attributes and Operations, select“Operations: Permission to Invoke”. Click on “Create Policy”
- In Attributes and Operations, select“Operations: Permission to Invoke”. Click on “Create Policy”
-
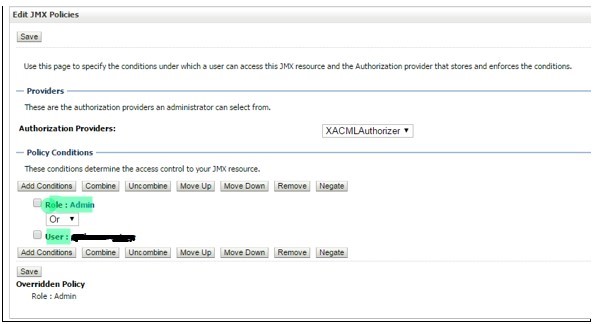
- Click on“Add Condition”-> Select “User” in “Predicate List” -> click next -> type User Argument Name (Username for which you want to provide access) -> click “add” and then “Finish”.
- Click on“Add Condition”-> Select Role in “Predicate List” -> click next -> type Role Argument Name (Admin) -> click “add” and then “Finish”.
-
- User should now be able to access JMS messages.
Note: If you do not see “JMX Policy Editor” option, it means that realm hasn’t been configured to delegate MBean authorization.